Uppsala Architecture Research Team
Shared Resource Sensitivity
This research quantitatively answers the question: "How much does the shared cache or bandwidth allocation affect application performance and resource usage." To do so, we use run an application that steals the shared resource and measure the resulting impact on the target application. By running such an application we effectively add a knob to the machine that allows us to control the amount of the shared resource available to the application. Since we capture this data on commodity hardware, we capture all the effects of the hardware and operating systems, including prefetching, VM, DRAM behavior, etc. However, to make this method accurate, we have to be careful to not steal any resources other than the shared resource we are interested in.
Bandwidth Bandit: Stealing Shared Bandwidth
The Bandwidth Bandit steals system bandwidth by accessing data in carefully chosen sequential and random access patterns that avoid polluting the cache hierarchy. (E.g., we design the pattern to ensure that we only use a very limited number of sets in the cache.) This work demonstrates that there is little correlation between bandwidth consumption and sensitivity, by quantitatively analyze whether an application is latency sensitive (e.g., slows down as soon as there is any bandwidth contention) or bandwidth sensitive (e.g., only slows down when bandwidth is exhausted).
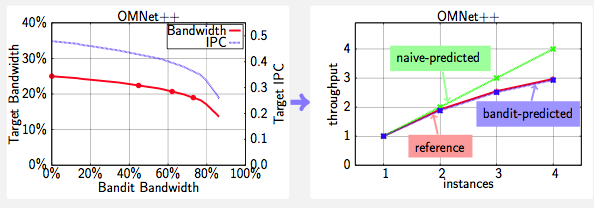
Using Bandit Data to predict multicore scaling for bandwidth-bound applications. Poster
- Bandwidth Bandit: Quantitative Characterization of Memory Contention. In Proc. 11th International Symposium on Code Generation and Optimization: CGO 2013, pp 99-108, IEEE Computer Society, 2013. (DOI).
- Bandwidth bandit: Quantitative characterization of memory contention. In Parallel Architectures and Compilation Techniques - Conference Proceedings, PACT, pp 457-458, 2012. (DOI).
Cache Pirate: Stealing Shared Cache
The Cache Pirate steals shared cache by accessing data in a carefully chosen access pattern to maximize the likelihood that it will keep data in the cache. To ensure that the pirate has stolen the correct amount of cache, we monitor its shared cache miss ratio: as long as the pirate is not missing in the cache we know it must have its full data set in the cache, and therefore we know how much cache it has stolen and that it is not consuming off-chip bandwidth. The cache quantitative cache sensitivity measurements provided by the Cache Pirate give detailed data on how an application's performance and bandwidth demands change with cache allocation. For cache-limited applications, this data can also accurately predict multicore scaling.
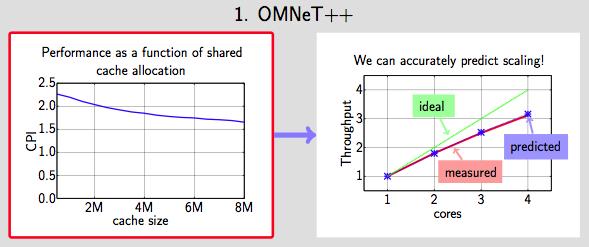
Using Pirate Data to predict multicore scaling for cache-bound applications. Poster
- Cache Pirating: Measuring the Curse of the Shared Cache. In Proc. 40th International Conference on Parallel Processing, pp 165-175, IEEE Computer Society, 2011. (DOI).
The Cache Pirate was chosen as the Best Paper of ICPP 2011.


